The group behind the cyberattack against the National Natural Gas System Operator proceeded to publish part of the documents they managed to intercept from the DESFA servers.
According to the first information, the material that has reached their hands is estimated at more than 350 GB, with the experts who have dealt with the case underlining that it is a “difficult case”.
As it appears, the hackers “infected” the operating system of the National Gas System Operator with a ransomware-type malware and thus managed to “infiltrate” all security barriers.
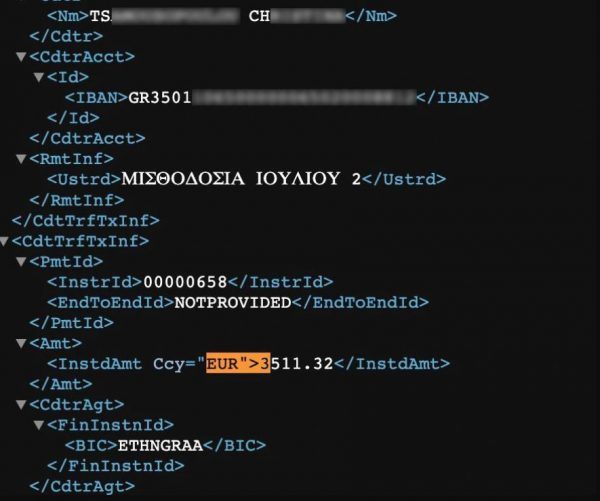
So far, it has not been known whether the perpetrators – who claim to have at their disposal crucial customer and employee information – have demanded a ransom from DESFA, with the managers of the Operator stressing that there has been no communication with the hackers.

The perpetrators are known to the FBI
A group of cyber extortionists known to the American authorities appears to be behind the attack on the National Natural Gas System Operator in Greece.
According to the FBI, this group is responsible for attacks on 52 organizations and companies in the last two years.
As reported by Kathimerini newspaper, the Ragnar Locker group allegedly claimed responsibility for the cyber attack with posts on the dark Internet, while publishing screenshots from various DESFA files allegedly in its possession.
According to the FBI, the Ragnar Locker group’s specific software was first used in April 2020, with the perpetrators attempting to digitally hold their targets’ electronic files hostage. Also, as the US authorities emphasize, the victims are mainly related to the energy and construction sectors.
At the same time, as the FBI notes in its relevant report, the Ragnar Locker team after the cyber attack are attempting to determine the location of the terminals used to inject the malware. If the target is found to be located in Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, Uzbekistan, Ukraine or Georgia, then the malware is disabled.
The timeline of the attack
The National Natural Gas System Operator (DESFA) announced on August 20 that it received a cyberattack on part of its IT infrastructure by cybercriminals who tried to gain illegal access to electronic files and with a confirmed impact on the availability of certain systems and the possible leakage of a number of files and certain data.
However, as it notes in an announcement “it managed to ensure and continue the operation of the National Natural Gas System (NSGS) in a safe and reliable manner”.
It is also underlined that “the management of DESFA continues to operate smoothly and DESFA continues to supply natural gas to all entry and exit points of the country safely and adequately”.
“We are investigating the root causes of the attack and have mobilized teams of technical and specialist experts to assist us in this matter, as well as to restore the systems to normal operation, as soon as possible. To protect our customers and partners, we have proactively disabled most of our IT services. We are gradually restoring our information and operational systems” emphasized DESFA, adding: “We have already informed all the competent authorities and organizations and we continue to work closely with the Ministry of Digital Governance, the Data Protection Authority, the Electronic Crime Prosecution of the Hellenic Police-ELAS, the National Defense General Staff as well as with the Ministry of Environment & Energy and the Energy Regulatory Authority to resolve the issue and minimize any potential impacts.”
“DESFA remains unwavering in its position not to negotiate with cybercriminals” concluded the company’s announcement.